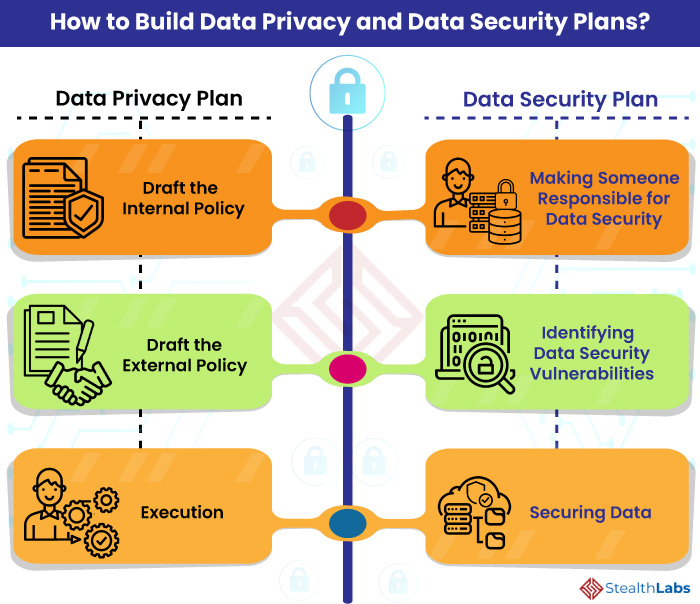
Best Data Security Software Process Flow For Company Online Database Security Elements PDF - PowerPoint Templates
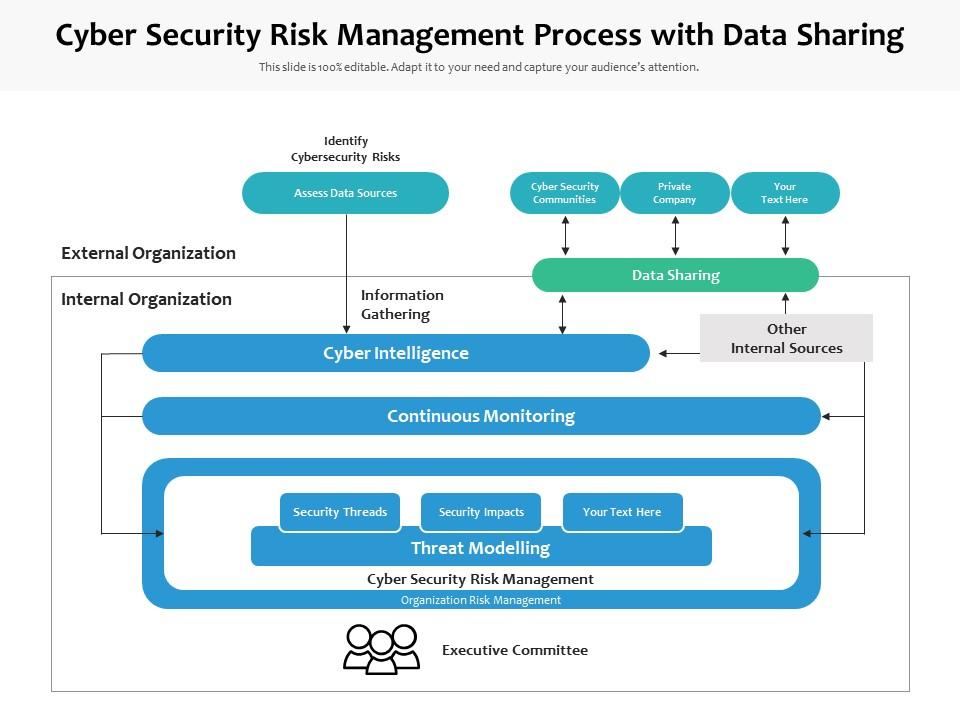
Cyber Security Risk Management Process With Data Sharing | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

8 IT Security Processes to Protect and Manage Company Data | Process Street | Checklist, Workflow and SOP Software
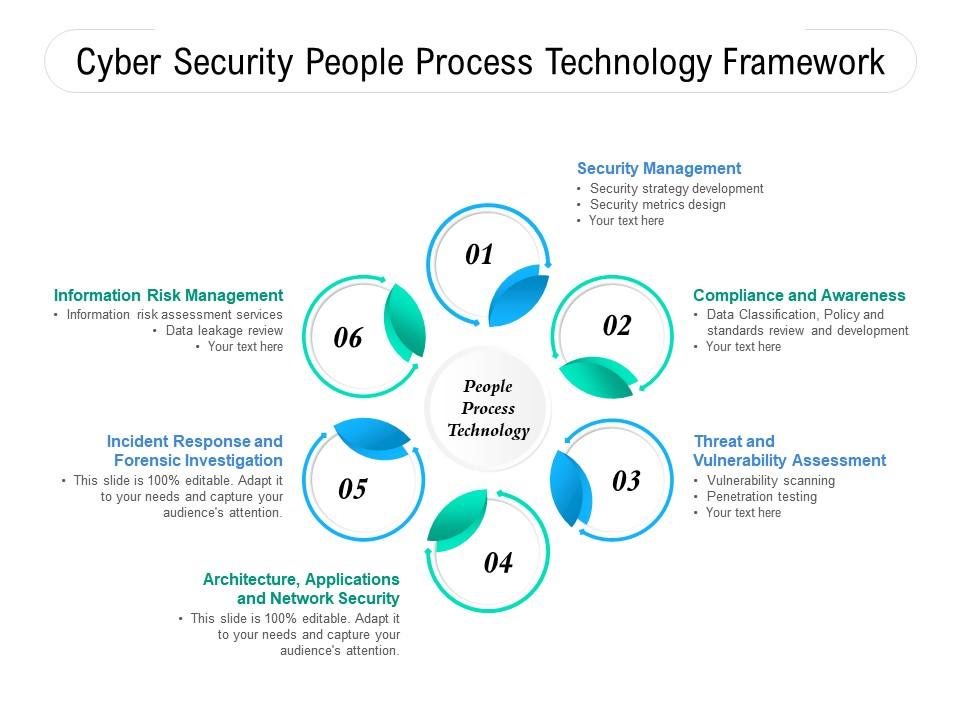





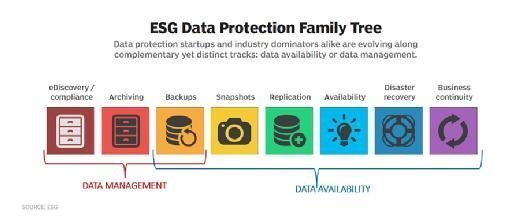



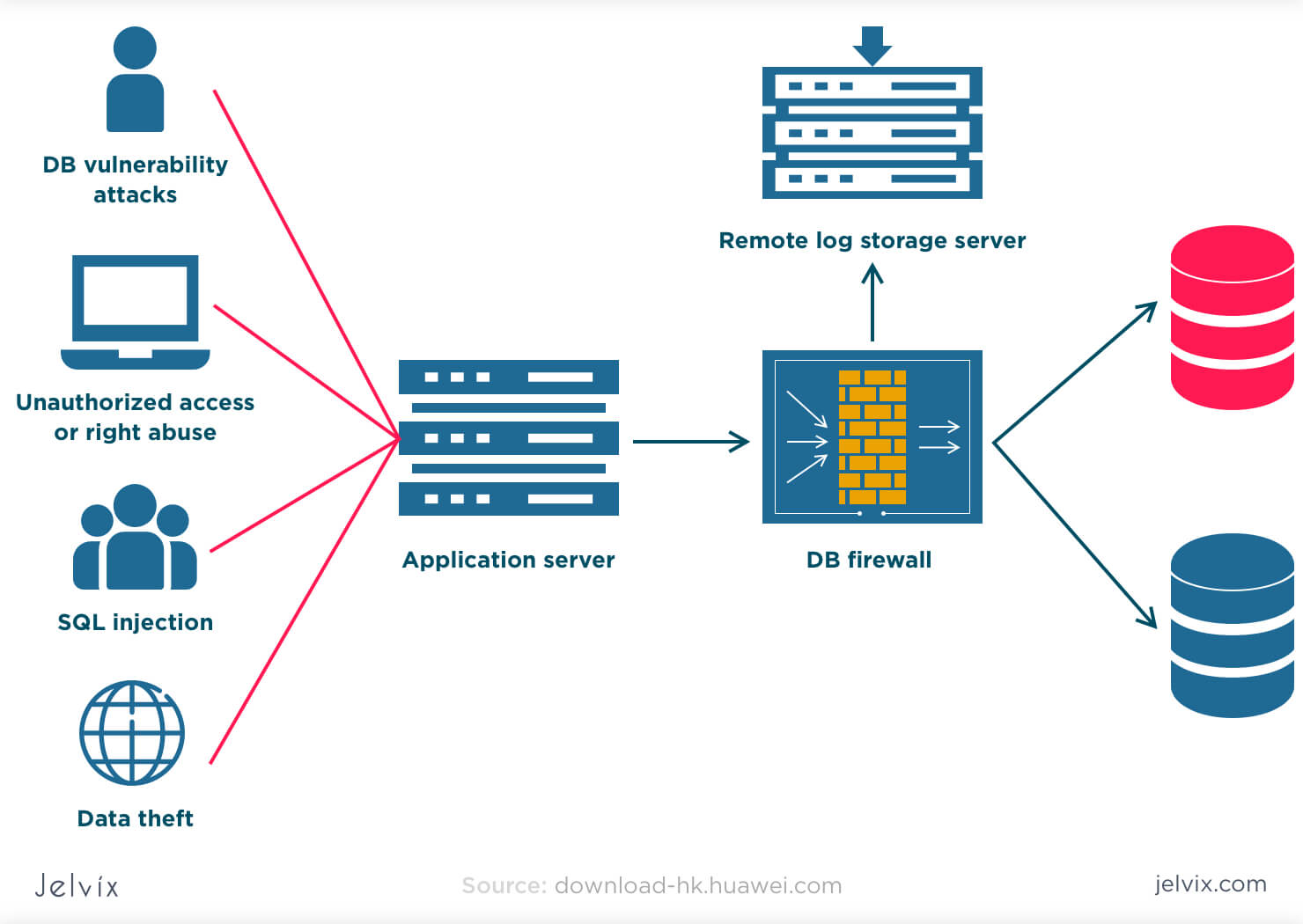

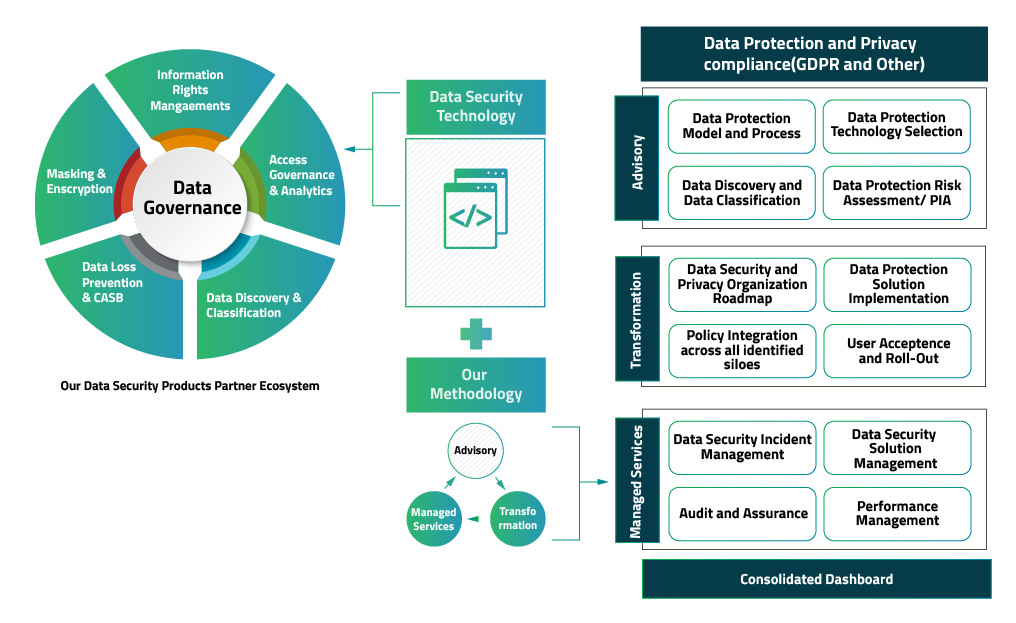
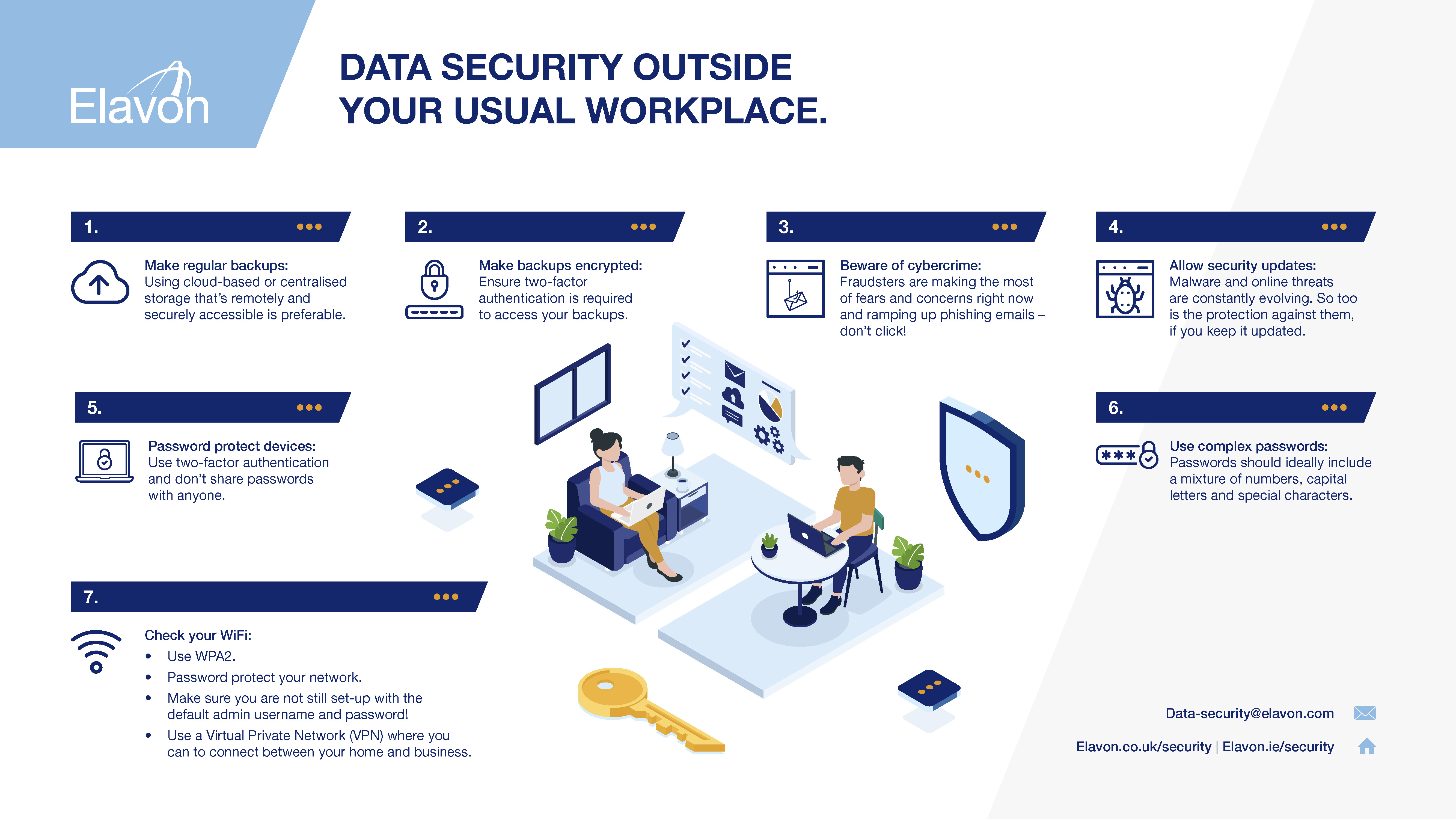
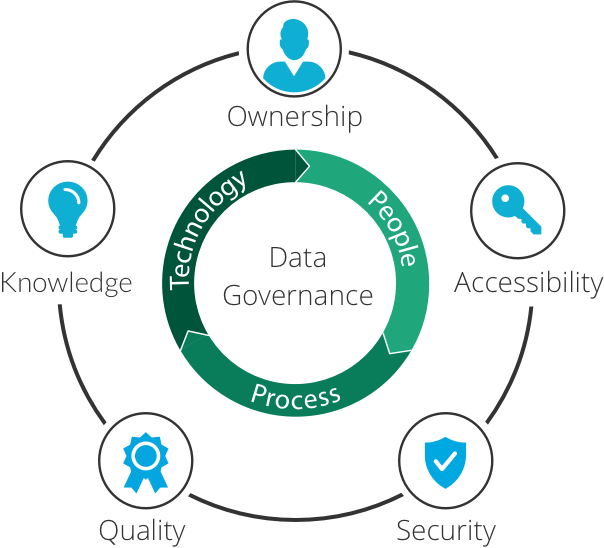




![Data Privacy vs. Data Security [definitions and comparisons] – Data Privacy Manager Data Privacy vs. Data Security [definitions and comparisons] – Data Privacy Manager](https://dataprivacymanager.net/wp-content/uploads/2019/05/Difference-between-data-privacy-and-data-security.png)