How Backing Up Your Data Safeguards Your Business From a Disaster - Directive Blogs | Oneonta, NY | Directive

Personal Data Protection Bill, 2019 Provides Safeguards against Private Actors; State Gets Broad Exemptions
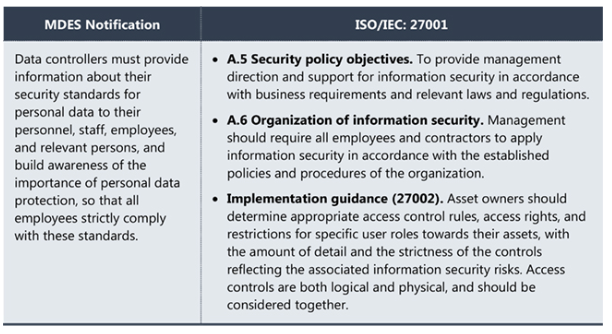
![PDF] Mapping 'Security Safeguard' Requirements in a data privacy legislation to an international privacy framework: A compliance methodology | Semantic Scholar PDF] Mapping 'Security Safeguard' Requirements in a data privacy legislation to an international privacy framework: A compliance methodology | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/4458e100c859f0f52e592a6f69bbc55a5b6902fe/3-Figure1-1.png)
PDF] Mapping 'Security Safeguard' Requirements in a data privacy legislation to an international privacy framework: A compliance methodology | Semantic Scholar

Unraveling Data's Gordian Knot : Enablers and Safeguards for Trusted Data Sharing in the New Economy

Proposed child data safeguards could do 'untold harm' to media companies, warn editors - Press Gazette